Why do KMS customer master keys have a 4kB size limit?
1. What is envelope encryption?
We want to encrypt our sensitive data to protect them. It might be a requirement in some industries (in the financial or medical industry, for example) that data we store in databases should be encrypted.
We can use a symmetric key called data key to encrypt our data. But if we leave the data key itself unencrypted, anyone getting it can access our data.
It’s the same as locking the front door but leaving the key in the keyhole (or put it under the mat). We have locked the door and still, anyone can open it.
Envelope encryption is the process of encrypting the data key itself.
If we have the data key encrypted, it won’t matter if bad actors get access to the data key because they won’t be able to use it. They would need the plaintext data key first to decrypt the data themselves.
Referring back to the door comparison, it’s like that we lock the door with the door key, put the door key in a box, and then lock the box itself. In case a thief put their hands on the box, they won’t be able to open the front door because they would need to get access to the door key first by opening the box.
2. How does it work?
It is all great, but what happens if a bad actor gets access to the key that encrypts the data key?
Well, we can encrypt the key that encrypts the data key using a third, different key.
But what about that third key? We can encrypt that one as well with a fourth key and so on and on.
Because this process can’t go forever, there has to be a key somewhere that sits at the end. This key is called the master key.
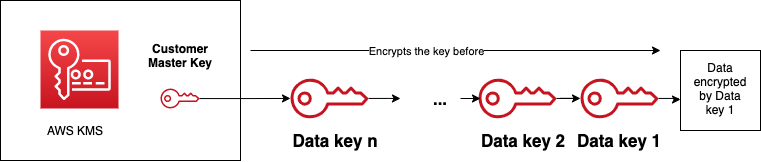
We need to ensure to store the master key in a safe place. If that key goes public, it doesn’t matter how many times our data are encrypted with various data keys, because a bad actor will get access to them.
3. AWS Key Management Service
AWS KMS stores these master keys (which can be AWS or customer-managed) in safe hardware security modules. The first element of the encryption chain is always protected, and it never leave AWS unencrypted.
The Encrypt and Decrypt APIs use a customer master key to encrypt and decrypt plaintext data, respectively. The size of these data can’t exceed 4kB, though.
Although this size is sufficient for encrypting a short text, like a password or private key, it’s not enough to manage data of a larger size.
It’s better to create a data key first using the GenerateDataKey API, encrypt the plaintext data with the data key we just created, and finally encrypt the data key with the customer managed master key. This is what AWS services (Amazon S3 or DynamoDB) do when server side encryption is enabled.
4. Conclusion
Let’s finally answer the question in the title of this post. It’s not needed to allow a size limit greater than 4kB because the use case of CMKs is to encrypt data of a small size. They are supposed to encrypt keys, passwords, and personal identifiers, and we use them for envelope encryption in our everyday AWS work. The size of these items should not exceed 4kB anyway.
Thanks for reading and see you next time.